Cybersecurity as competitive advantage in a world of uncertainty
The economy is on the minds of business leaders. C-suites recognize survival depends upon the ability to safeguard systems and information. They need to redesign for resilience—mitigate risk, strategically deploy assets and investments and assign accountability.
The approach
A key part of rapid digitalization, fueled by the pandemic, is accelerated cloud adoption. Together, digitalization and the Cloud Continuum have redefined not only enterprise boundaries and capabilities but also the attack surface, adding vulnerabilities that are beyond the reach of traditional responses. We cover common security blindspots, from automation to talent shortages and outline two routes to the cloud, each with their own risks and approaches.

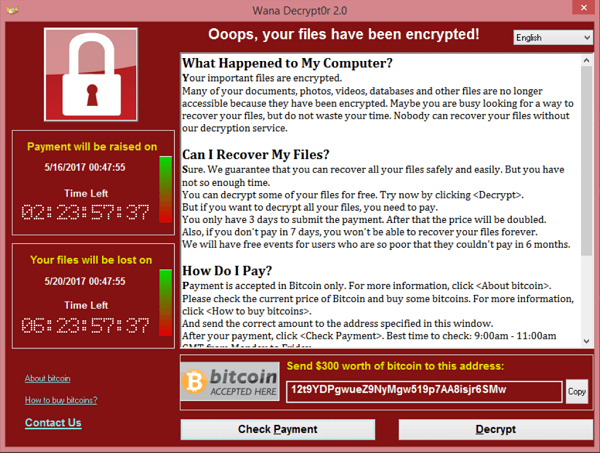
Ransomware and other types of cyber attacks have evolved—so too should your organizational approach to managing them. Ransomware is a threat to the entire business, with impacts downstream, upstream and across customers and stakeholders. From processes to people, cross-enterprise alignment is key to protecting value and ensuring operational continuity. Learn what ransomware attacks look like today and understand the priorities, challenges and steps involved in modernizing your response.
In ensuring the success of an organization’s cybersecurity efforts is critical. The responsability for setting the overall direction and strategy for the organization, including its approach to cybersecurity. the establishing policies and procedures to protect against cyber threats, allocating resources to support cybersecurity efforts, and communicating the importance of cybersecurity to the rest of the organization. its involved in monitoring the organization’s cybersecurity posture and taking any necessary steps to address any weaknesses that are identified. Additionally, also should ensure that the organization is continuously learning about and adapting to new cyber threats, and that it has the necessary expertise and resources in place to defend against those threats.

The State of Cybersecurity Resilience research explores insights from annual survey of 4,744 global respondents. The report examines the extent to which organizations prioritize security, how comprehensive their security plans are and how their security investments are performing. It also examines how strength of alignment between cybersecurity strategy and business strategy impacts cyber resilience. We identified four levels of cyber resilience. At the head of the pack is a group of Cyber Champions—organizations that strike a balance, not only excelling at cyber resilience, but also aligning with the business strategy to achieve better business outcomes.

Services by technology
Analytics
Unlock the strategic value of enterprise data and build an insight-driven organization.
Application services
Boost your cloud investment by transforming the way you manage applications.
Artificial intelligence
Create intelligent workflows that utilize AI, data and analytics, and turn AI aspirations into tangible business outcomes.
Blockchain
Into proven design methodologies and composable capabilities that can accelerate positive business outcomes.
Cloud computing
Provides hybrid, open and managed cloud services across multiple security-rich cloud environments.
Hybrid cloud
Accelerate business agility and growth continuously modernize your applications on any platform using a hybrid cloud approach.
Cybersecurity
Transform your business and manage risk with a global industry leader in cybersecurity consulting, cloud and managed security services.
E-commerce
Engineer personalized customer experiences built on a seamless, industry-specific e-commerce platform.
Helping businesses accelerate their journey to cloud
Change isn’t constrained to business or industry. It’s happening throughout the world, every moment of every day. For enterprise leaders, Borderless Consulting helps the complexity of decision . To compete and win requires a trusted partner with the experience and skills to bring opportunity into focus and operationalize positive change quickly — a partner who can enable confident decisioning that keeps you ahead of the market.
Capabilities
Cyber Strategy
Define cyber, risk mitigation and regulatory strategies, aligning security to business priorities.
Cyber Protection
Protect the business as it transforms applying zero trust principles to secure the entire digital core.
Cyber Resilience
Pressure test defenses, understand emerging threats and prepare and respond quickly to attacks.
Cyber Industry
Embed security to build resilience and mitigate risk across critical areas of the value chain.
Manage risk and accelerate your business innovation and security at the same pace
With the industry’s broadest portfolio of consulting and global managed security services, Borderless Consulting services can help you quantify and prioritize your risks. Our professionals deliver industry-leading assessments and security strategies to many of the world’s largest enterprises, including critical strategies such as zero trust. As a trusted advisor, Borderless Consulting can extend your team, help detect and respond to threats, and unify your organization on security priorities to accelerate business transformation.
Security challenges to your business
Partner with Borderless Consulting security services to help your transformation journey
Having cybersecurity keep up with the pace of innovation is a challenge many organization leaders like you face. You need an approach that manages current and anticipated risks without adversely affecting the progress of your business growth. A clear and aligned strategy to assess your enterprise’s overall maturity and gaps is necessary for you to build security into your digital strategy and transformation initiative. Without such a strategy, you may question if and how you can effectively respond to threats that continue to grow exponentially.
Your fears are well founded. These figures indicate just how data breaches have become all too common and too costly for enterprises like yours when not addressed.
USD 4.35 million
Global average total cost of a data breach in 2022
USD 871,686
Global average for theft of credentials in 2022
2,000%
Growth of attacks on operational technology between 2018 and 2022
63%
of enterprises see cybersecurity as a business enabler
42%
of enterprises include cybersecurity in the planning of all new deployments
83%
of enterprises have no plans to reduce their cybersecurity budgets, despite the decrease in IT spending caused by COVID-19
61%
of all breaches involve credentials, whether they be stolen via social engineering or hacked using brute force.
4100
publicly disclosed data breaches occurred in 2022 equating to approximately 22 billion records being exposed. Cyber security publication Security Magazine reported that the figures for 2022 are expected to exceed this figure by as much as five percent
The common causes of Data Breaches
- Insider Threats Due to Misuse of Privileged Access.
- Weak and Stolen Passwords
- Unpatched Applications
- Malware
- Social Engineering
- Physical Attacks
Biggest breaches in 2022
- Twitter accused of covering up data breach that affects millions
- More than 1.2 million credit card numbers leaked on hacking forum
- Personal and medical data for 11 million people accessed in Optus data breach
- Hacker attempts to sell data of 500 million WhatsApp users on dark web
- 9.7 million peoples’ information stolen in Medibank data leak
- Hacker allegedly hits both Uber and Rockstar
- Student loan data breach leaks 2.5 million social security numbers
- SHEIN fined US$1.9mn over data breach affecting 39 million customers
- Revolut data breach exposes information for more than 50,000 customers
“When there is consensus among cybersecurity experts about best practices, standards, and protocols, it helps to create a strong and resilient defense against cyber threats. This is especially important given the increasing reliance on technology in our daily lives and the increasing sophistication of cyber attacks.”
Julio Verissimo
President & CEO – Borderless Consulting
The responce to these challenges
Additionally, hard-to-manage cybersecurity portfolios are the main inhibitor of security capability improvement.
The answer to all of these challenges is Borderless Consulting security services, which provides the modern, open, unified approach to security that you need.
With Borderless Consulting security services, you get proactive help to align, protect, manage and modernize your security in the following ways:
Align your security strategy with your business.
Protect your digital assets, users and data.
Manage your defenses against growing threats.
Modernize your security with an open, multicloud strategy.
The new Fusion Centers
Combining managed security services, market-leading advanced analytics and intelligent automation, our cyber defense incubation centers help organizations out-innovate attackers every single day.

Cyber Fusion Center
Borderless Consulting purposal to build, one-of-a-kind Cyber Fusion Center for operational technology (OT) security and industrial control systems (ICS).

Global Cyber Fusion Center
To have collective of global security professionals, leading data scientists, renowned academic researchers as well as technology and alliance partners for global monitoring

Distribuited Cyber Fusion Center
A Cyber Fusion Center to combines threat intelligence, adversary simulations, incident response and cybersecurity R&D for most imediate responce

